Twitpic, EXIF and GPS: I Know Where You Did it Last Summer
Modern cell phones frequently include a camera and a GPS. Even if a GPS is not included, cell phone towers can be used to establish the location of the phone. Image formats include special headers that can be used to store this information, so called EXIF tags.
In order to test the prevalence of these tags and analyze the information leaked via EXIF tags, we collected 15,291 images from popular image hosting site Twitpic.com. Twitpic is frequently used together with Twitter. Software on smart phones will take the picture, upload it to twitpix and then post a message on Twitter pointing to the image. Twitpic images are usually not protected and open for all to read who know the URL. The URL is short and incrementing, allowing for easy harvesting of pictures hosted on Twitpic.
We wrote a little script to harvest 15,291 images. A second script was used to analyze the EXIF information embedded in these images. About 10,000 of the images included basic EXIF information, like image resolution and camera orientation. 5247 images included the Camera Model.
Most interestingly: 399 images included the location of the camera at the time the image was taken, and 102 images included the name of the photographer. Correlating the camera model with the photographer field, we found that it was predominantly set for the Canon and Nikon cameras. Only few camera phones had the parameter set.
GPS coordinates where only set for phones, with one single exception (a Nikon Point and Shoot camera, which does not appear to come with a build in GPS. The location may have been added manually or by an external GPS unit). The lion share of images that included GPS tags came from iPhones.
The iPhone is including the most EXIF information among the images we found. The largest EXIF data set we found can be found here. It not only includes the phone's location, but also accelerometer data showing if the phone was moved at the time the picture was taken and the readout from the build in compass showing in which direction the phone was pointed at the time.
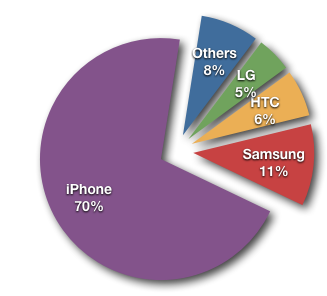
Figure 1: Pictures with GPS coordinates broken down by Phone manufacturer.
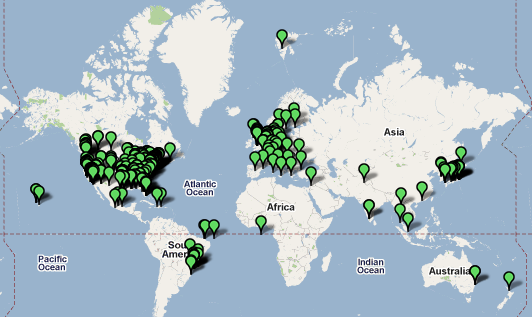
Figure 2: Geographic Distribution of Images
Now the obvious question: Anything interesting in these pictures? The images all the way up north shows an empty grocery store (kind of like in the DC area these days). The picture at the Afghan - Pakistan border shows a pizza... Osama got away again I guess.
The scripts used for this can be found here: http://johannes.homepc.org/twitscripts.tgz (two scripts, also needs "exiftools" to pull out the data).
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
Datacenters and Directory Traversals
We got a couple of interesting emails late in the shift today so I thought I'd lump them into one diary.
Tommy asked, "What happens when a SANS taught security guy builds a datacenter?" You have to see this to believe it. He used a former class III safety deposit bank vault and put photos of the construction online at http://www.tylervault.com/how.htm. Nice job!
Ron told us that he "wrote an Nmap script this week to detect a VMWare vulnerability, CVE-2009-3733. It's a nasty one because it's trivial to exploit and potentially incredibly damaging (you can download any file from the filesystem)." The details of the vulnerability were released last weekend at Shmoocon. It's a directory traversal issue - remember them? I thought we figured out ten years ago that this was a Bad ThingTM. I guess VMWare didn't get the message. Ron's Nmap script and a description of the issue is at
http://www.skullsecurity.org/blog/?p=436.
Marcus H. Sachs
Director, SANS Internet Storm Center
Vulnerability in TLS/SSL Could Allow Spoofing
Microsoft released a bulletin yesterday about a potential problem in TLS/SSL that could allow spoofing. From their bulletin:
Microsoft is investigating public reports of a vulnerability in the Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols. At this time, Microsoft is not aware of any attacks attempting to exploit the reported vulnerability.
As an issue affecting an Internet standard, we recognize that this issue affects multiple vendors. We are working on a coordinated response with our partners in the Internet Consortium for Advancement of Security on the Internet (ICASI). The TLS and SSL protocols are implemented in several Microsoft products, both client and server, and this advisory will be updated as our investigation continues.
As part of this security advisory, Microsoft is making available a workaround which enables system administrators to disable TLS and SSL renegotiation functionality. However, as renegotiation is required functionality for some applications, this workaround is not intended for wide implementation and should be tested extensively prior to implementation.
Upon completion of this investigation, Microsoft will take the appropriate action to protect our customers, which may include providing a solution through our monthly security update release process, depending on customer needs.
More details are in their bulletin and we'll let you know if we hear anything more. We have not received any reports of in-the-wild exploitation of this potential vulnerability.
Thanks, Kurt and Cheryl, for bringing this to our attention!
Marcus H. Sachs
Director, SANS Internet Storm Center


Comments